The Future of AI: Why Having an AI Acceptable Use Policy Is Important

In an era where artificial intelligence (AI) is rapidly evolving and permeating various aspects of business operations, the need for an AI Acceptable Use Policy (AUP) has become increasingly apparent. As companies try to understand how they can leverage AI, they must also acknowledge the ethical, legal, and societal implications that accompany such advancements. Because […]
Data Privacy Week: Take Control of Your Data

It’s that time of year again for the National Cyber Security Alliance’s (NCSA) Data Privacy Week. This year Data Privacy Week is January 21 – 27th 2024. Data Privacy Week is an annual event initiated by the NCSA to raise awareness about the importance of privacy and protecting personal information. The NCSA, a non-profit organization, […]
Cybersecurity Awareness Month: Secure Our World

October is here, and with it comes Cybersecurity Awareness Month, a time to focus on safeguarding our digital lives. This is the 20th year of the Cyber Security Awareness Month campaign and the theme this year is Secure Our World. Secure Our World is meant to remind us that there are simple ways to protect […]
Steps to Protect Your LinkedIn Account

LinkedIn is undoubtedly one of the most popular platforms for professionals, job seekers, and businesses. With over 774 million users worldwide, it’s a treasure trove of career opportunities, networking, and industry insights. However, like any other online platform, it’s not immune to security threats. In the past, LinkedIn has faced data breaches and hacks, compromising […]
What to Do If Your Personal Information Has Been Involved in a Breach

The list of popular companies that many of us interact with or use for services that have had breaches continues to grow in 2023. With cyberattacks becoming more sophisticated, knowing how to respond is crucial if you discover that your personal data has been involved in a breach. In this blog post, we will guide […]
The Power of Single Sign-On with Multi-Factor Authentication

In today’s rapidly evolving digital landscape, businesses face increasing challenges in securing their systems and data. As technology advances, so do the tactics employed by cybercriminals. One powerful tool to combat these threats is the implementation of Single Sign-On (SSO) with Multi-Factor Authentication (MFA). This combination offers a robust and comprehensive security solution while simplifying […]
3 Reasons Proactive Security Awareness Should Matter to You

Social engineering attacks remain one of the top cybersecurity threats to companies in 2023. According to recent research, businesses experience an average of over 700 social engineering attacks annually, and these attacks use tactics such as phishing and ransomware to exploit a lack of attention, awareness, and time to assess the threat. To combat these […]
Data Privacy Week: Understanding the Importance of Protecting Your Digital Footprint

As we all continue to navigate an ever-expanding digital landscape, we must be aware of the trail of data we leave behind. This year, during Data Privacy Week, which is taking place from January 22nd-January 28th, we are shining a spotlight on the importance of protecting our digital footprints and holding organizations accountable for respecting our privacy.
End of 2022 Things to Consider

In 2022, there were 15 million data breaches worldwide in the third quarter of the year alone, meaning the risk of cyberattacks remains high. As the end of the year approaches, it is a good time to think about the safety of both your personal and business systems, apps, and accounts.
See Yourself in Cyber: Why People Are the Center of Cybersecurity

In 2004, October was declared Cybersecurity Awareness Month. Dedicating October to cybersecurity helps raise awareness about the importance of protecting our personal and professional information. As we see this focus on cybersecurity remain central to business strategies year after year, it is a reminder that we are still battling security risks, old and new. This […]
SOHO Attacks: Why Home Offices Need to be Part of Your Organization’s Security Strategy

What is ZuoRAT and how does it work? Remote Access Trojans (RAT’s) have existed since the 1990’s. They are malicious software designed to remotely control an infected computer, while remaining undetectable. What makes the newly discovered ZuoRAT unique is that it appears to be a highly organized, potentially state-sponsored hacking campaign specifically targeting remote workers […]
The Three Ps of Cybersecurity

Cyber threats and attacks are rising, costing companies money and time. According to the FBI, in 2021 alone, companies lost around $6.9 billion. So how can organizations protect themselves? In this post, we’ll explain the three Ps that any company should have as part of their security defense and how you can utilize them to prevent […]
Data Privacy Week Concepts to Remember All Year Long

In 2022, Data Privacy Week is taking place from January 24-28. It is crucial to raise awareness about data privacy during this week-long initiative. However, data privacy concepts remain essential for securing and managing personal information all year. Learn more about Data Privacy Week and how you can do more to protect your data privacy in this […]
Looking Beyond Cybersecurity Awareness Month

October has been dedicated to Cybersecurity Awareness Month every year since 2004. However, as this year’s Cybersecurity Awareness Month comes to an end, your Data Evolution experts are here to remind you that cybersecurity matters every day. Join us as we review why Cybersecurity Awareness Month matters and how we can look beyond this month […]
Managed Network Infrastructure Security: Why It Matters

Your network infrastructure takes time and effort to strategize and develop. Any compromise to your network or infrastructure can disrupt connectivity, communication, and other operational activities. Network infrastructure security is crucial to your productivity. Protecting your network infrastructure ensures that it functions optimally and seamlessly. However, network infrastructure security can be complicated due to the […]
5 Ways to Create a Strong Password
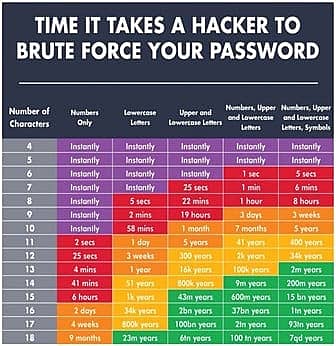
Your passwords are like the lock to your house. You would not offer the keys to random people or install a simple lock that any criminal could pick easily. Any compromise to your password security could potentially hurt your credit, financial health, identity, and more. A strong password can help protect you from these situations. […]
3 Things You Should Know About Managed Endpoint Security

Network devices such as laptops, tablets, or servers make it easier than ever for organizations to collaborate and accomplish work together. However, these devices, also called endpoints, also provide many potential entry points for threats such as viruses, unauthorized access, and other malicious activity. Managed endpoint security is necessary for organizations such as biotechs and […]
3 Reasons Proactive Security Awareness Should Matter to You

These days, social engineering attacks are one of the top threats to your company’s cybersecurity. A recent study found that, on average, organizations get targeted by more than 700 social engineering attacks per year. This type of threat includes techniques such as phishing and ransomware, and it relies on a lack of awareness, attention, and time […]
End-User Security Training from Onboarding to Offboarding

If you read or watch the news, then it is no surprise that companies’ electronic systems get compromised all the time, whether big or small. The biotech and life science industry is no stranger to these threats. Even with antivirus and antimalware systems in place, breaches are still possible through the vulnerable path of your […]
5 Key Cybersecurity Musts for Life Science Companies

Life science companies regularly deal with intellectual property and expensive lab equipment, making them an appealing target for cybercriminals. This is a major issue on two crucial fronts: Cybersecurity threats can disrupt your essential research and development of highly sought-after pharmaceuticals. There is no shortage of diseases and conditions that need treatments and cures, making […]
Identifying Risks to Your Data Security

A data breach has the potential to cause reputation damage, financial ramifications, and legal liability. Any company with sensitive data or intellectual property must ensure their work is secure. Data security is an escalating issue for life sciences companies in particular: 40% of cyberattacks on life sciences companies reported to the media since 2017 took place […]

